PPT) 1 Adaptively Attribute-Hiding ( Hierarchical ) Inner Product Encryption 2012 / 4 / 18 Tatsuaki Okamoto ( NTT ), Katsuyuki Takashima ( Mitsubishi Electric - DOKUMEN.TIPS
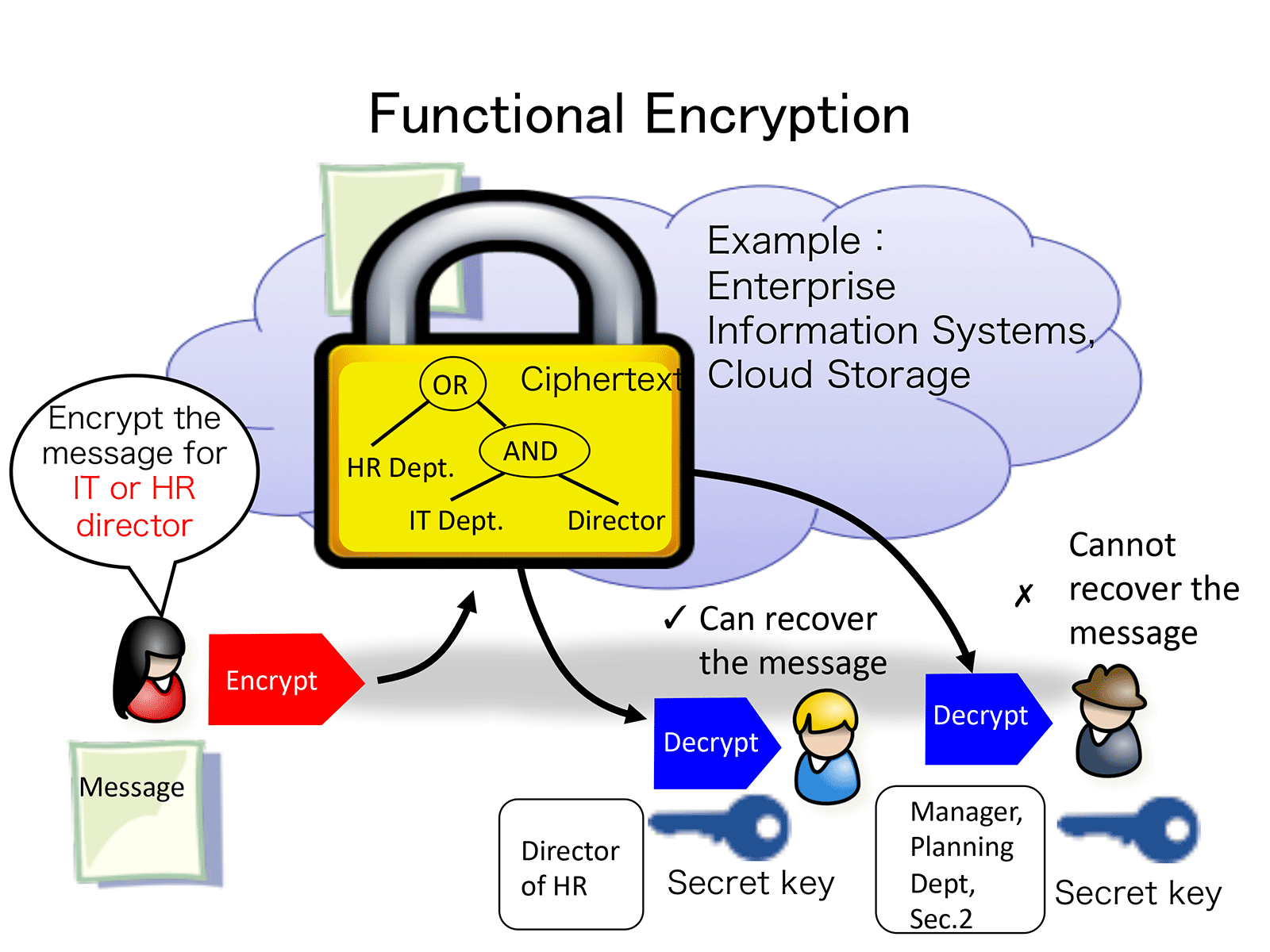
Cryptography with Advanced Functionality - Research - Advanced Cryptography Research Team | Cyber Physical Security Research Center - AIST
![PDF] Hierarchical identity-based inner product functional encryption by Ge Song, Yuqiao Deng, Qiong Huang, Changgen Peng, Chunming Tang, Xiaohua Wang · 10.1016/j.ins.2021.05.062 · OA.mg PDF] Hierarchical identity-based inner product functional encryption by Ge Song, Yuqiao Deng, Qiong Huang, Changgen Peng, Chunming Tang, Xiaohua Wang · 10.1016/j.ins.2021.05.062 · OA.mg](https://og.oa.mg/Hierarchical%20identity-based%20inner%20product%20functional%20encryption.png?author=%20Ge%20Song,%20Yuqiao%20Deng,%20Qiong%20Huang,%20Changgen%20Peng,%20Chunming%20Tang,%20Xiaohua%20Wang)
PDF] Hierarchical identity-based inner product functional encryption by Ge Song, Yuqiao Deng, Qiong Huang, Changgen Peng, Chunming Tang, Xiaohua Wang · 10.1016/j.ins.2021.05.062 · OA.mg
2-Step Multi-Client Quadratic Functional Encryption from Decentralized Function-Hiding Inner-Product

PPT – Fully Secure Functional Encryption: Attribute-Based Encryption and (Hierarchical) Inner Product Encryption PowerPoint presentation | free to view - id: 3bf96f-NTUzO
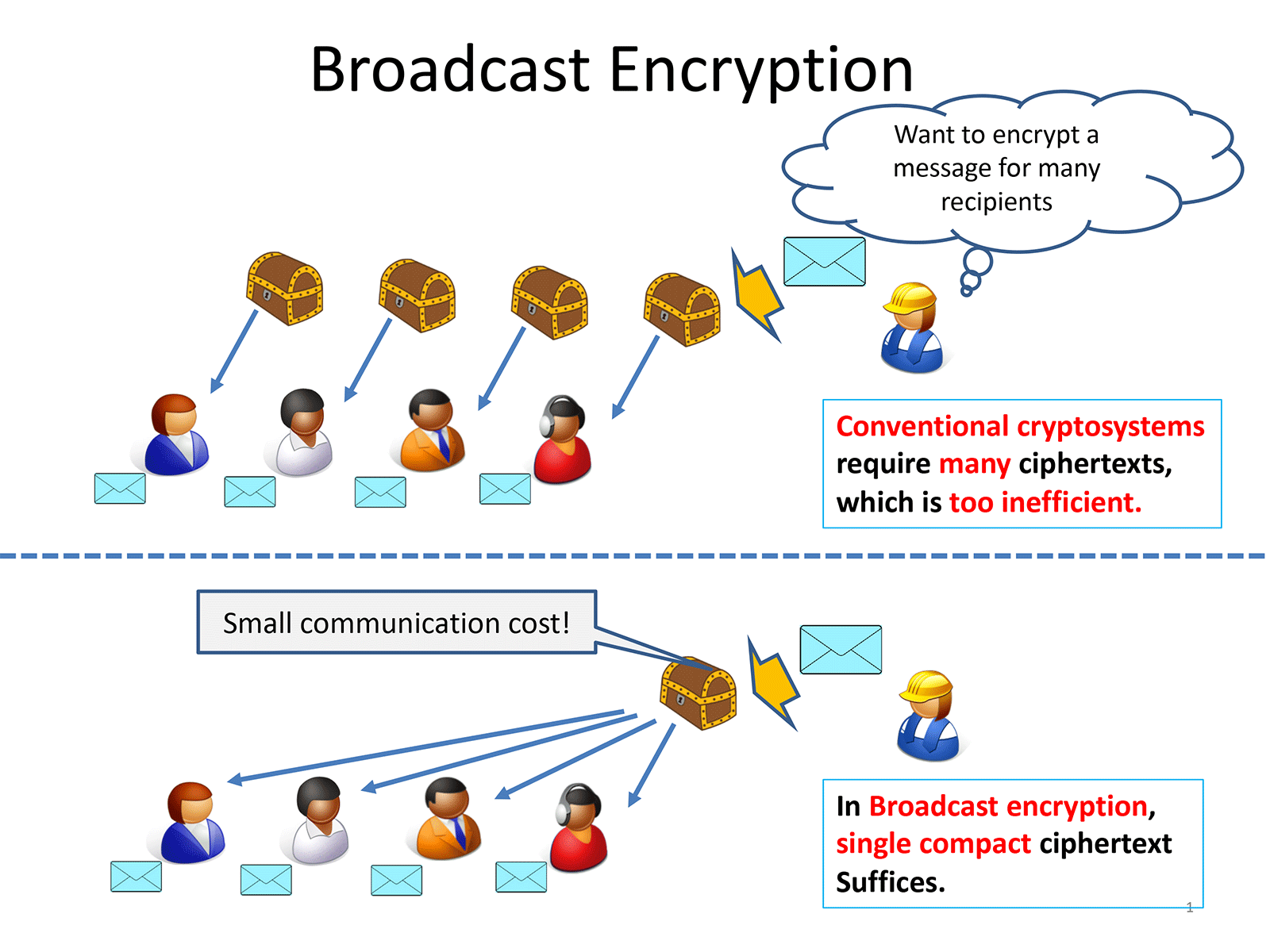
Cryptography with Advanced Functionality - Research - Advanced Cryptography Research Team | Cyber Physical Security Research Center - AIST
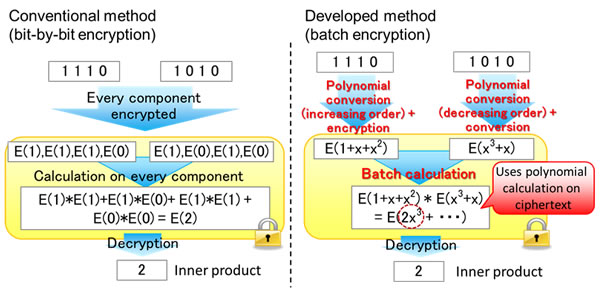
Fujitsu Develops World's First Homomorphic Encryption Technology that Enables Statistical Calculations and Biometric Authentication - Fujitsu Global

Fully Secure Functional Encryption: Attribute-Based Encryption and (Hierarchical) Inner Product Encryption Allison Lewko Tatsuaki Okamoto Amit Sahai The. - ppt video online download
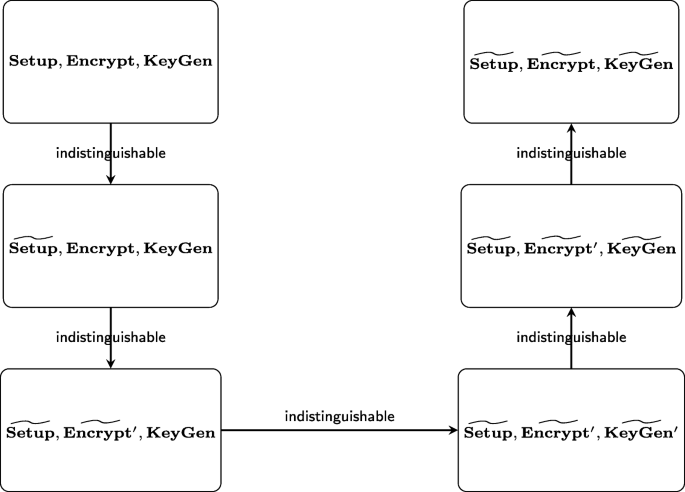
Efficient functional encryption for inner product with simulation-based security | Cybersecurity | Full Text
![PDF] An Efficient Cryptography-Based Access Control Using Inner-Product Proxy Re-Encryption Scheme | Semantic Scholar PDF] An Efficient Cryptography-Based Access Control Using Inner-Product Proxy Re-Encryption Scheme | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/fb79f18c0685f9786ce0ef495ff845e0ac50c142/2-Figure1-1.png)
PDF] An Efficient Cryptography-Based Access Control Using Inner-Product Proxy Re-Encryption Scheme | Semantic Scholar

Sensors | Free Full-Text | Efficient and Privacy-Preserving Energy Trading on Blockchain Using Dual Binary Encoding for Inner Product Encryption

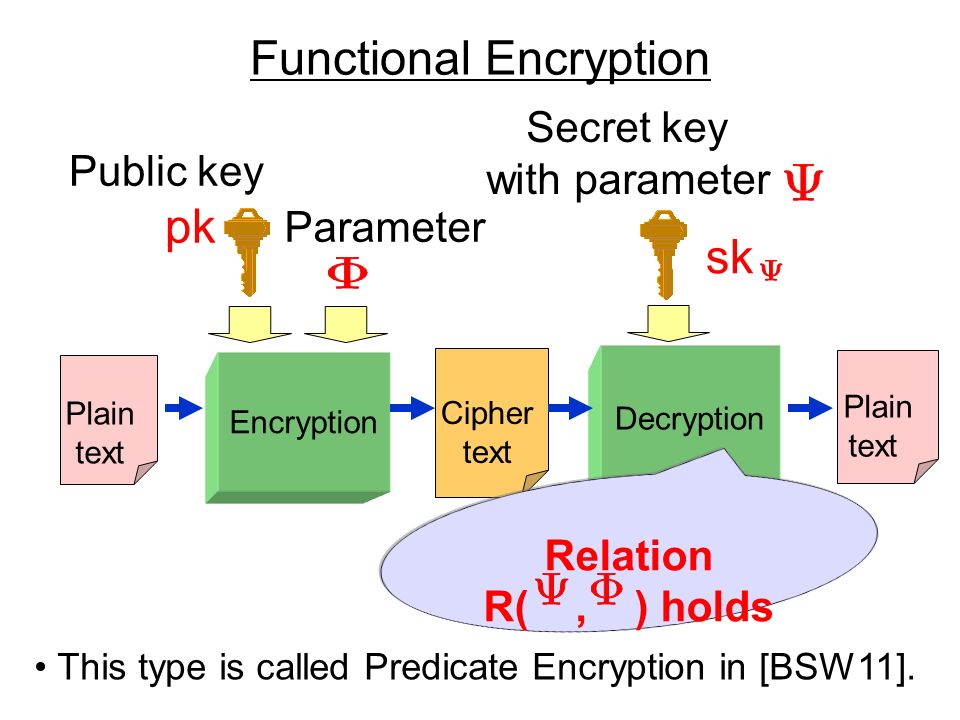


![PDF] Functional encryption for inner-product evaluations | Semantic Scholar PDF] Functional encryption for inner-product evaluations | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/40f98cf0dcac4be854d52a0f30febd042ee25a22/33-Figure3.1-1.png)